
US Army/Staff Sgt. William Howard
- In recent years, data from resources like fitness apps has been used to track the movements of US military personnel.
- Those incidents highlight the evolving challenge of securing personal information as adversaries embrace cyberwarfare.
- See more stories on Insider's business page.
In a world with technological inventions seemingly every month, US troops and special-operators are facing a whole different set of problems that no one could have imagined a few years ago.
In the past few years, a series of flaps involving US and Coalition special-operations forces and popular fitness applications, such as Strava or the Apple Watch, have jeopardized operational and personal security.
These flaps offer near-peer competitors, such as China and Russia, and even terrorist groups a glimpse behind the shadowy world of special-operations and intelligence that can be used against the commandos.
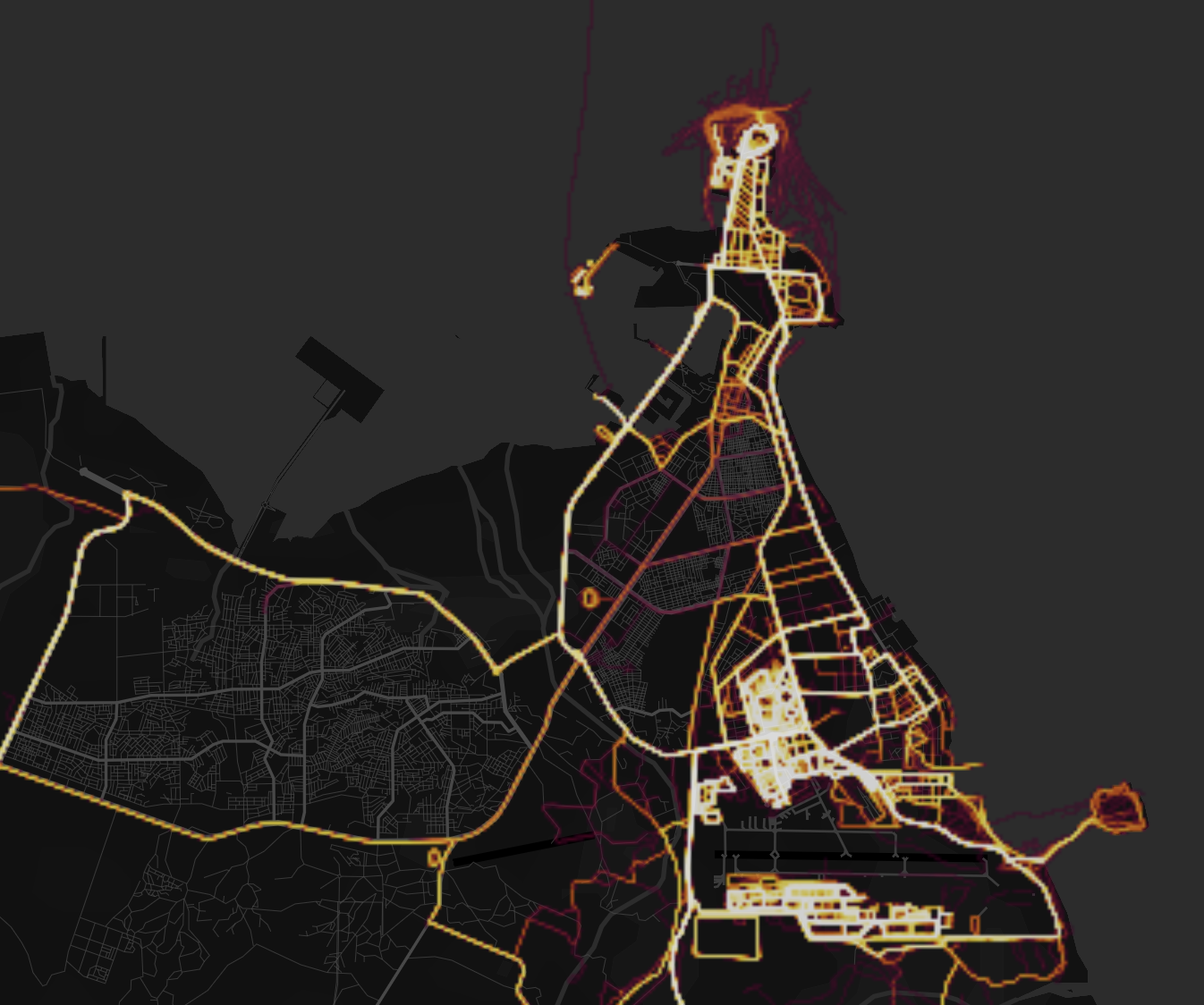
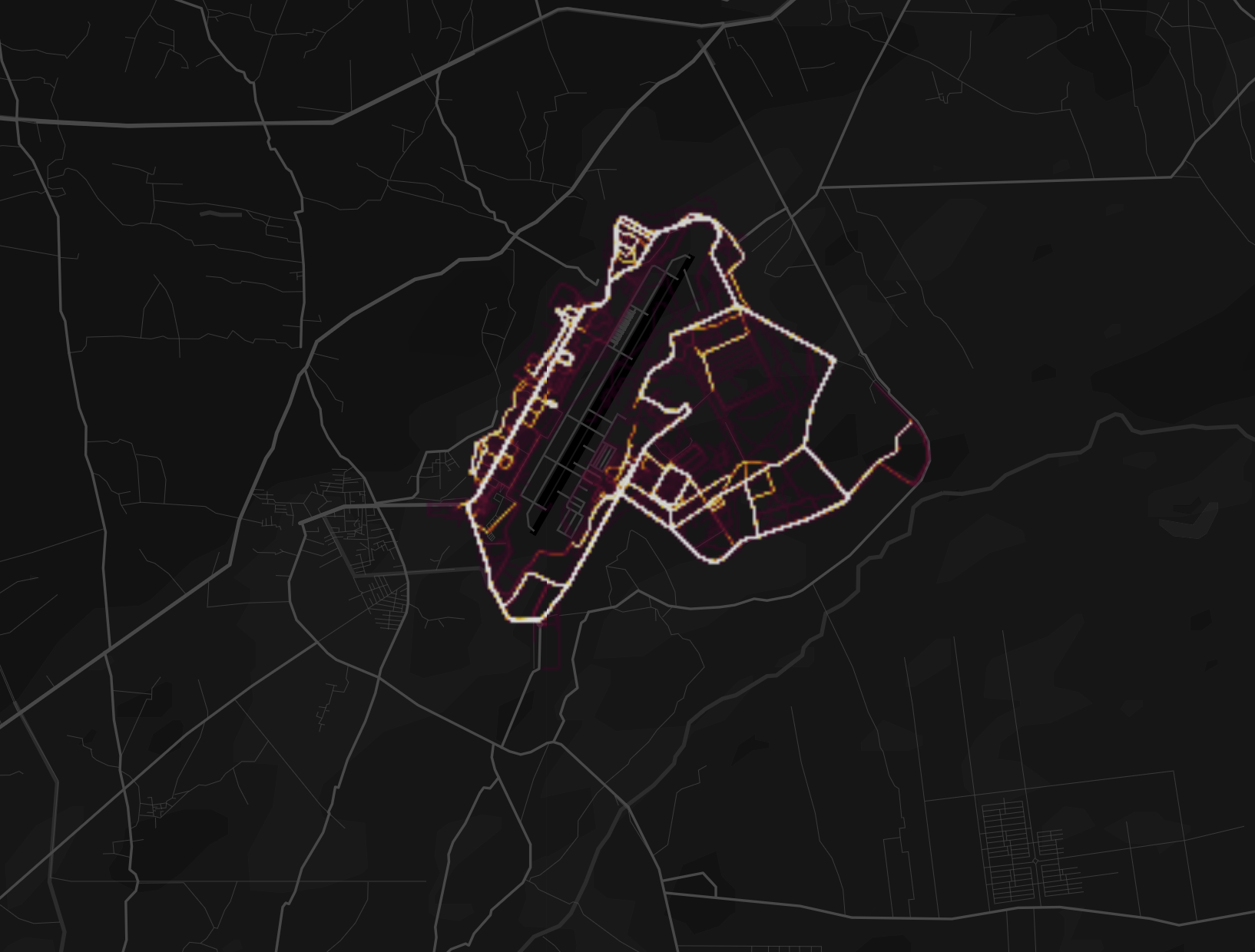
In 2018, reports revealed that the popular fitness tracker Strava could be manipulated to show the positions, bases, and even patrol routes of US troops in Syria, Afghanistan, and other countries.
Digital or electronic tracking doesn't only affect the US special-operations community. In 2020, journalists and open-source information researchers were able to manipulate Strava to track down British Special Air Service (SAS) operators in Syria and Somalia.
The manipulation of data didn't end there. The journalists and researchers were able also to track the SAS operators' fitness activities - and thus their pattern of life - in the UK by simply tracking the accounts they correctly surmised were associated with SAS operators.
'I can see you'
Strava
In a recent article, West Point's Modern War Institute expertly covered the modern dangers of electronic and digital signatures. The article discusses how SEAL Team 6's recent successful hostage-rescue operation in Niger was tracked by an open-source aviation site nearly in real-time.
Everyone, including China and Russia, now knows what aircraft the task force used, how the SEALs infiltrated and exfiltrated the target, and other relevant details about the capabilities of US Joint Special Operations Command (JSOC).
Similar sites that track maritime traffic also exist. Standard operating procedure during combat or confrontational operations, especially when using cover aircraft or ships, is usually to turn off the vessel's or aircraft's transmitter.
In August, for example, the Turkish research vessel Oruç Reis, which threatened to conduct illegal surveys in Greece's and Cyprus' exclusive maritime zones, risking a war, always turned its transmitter off when operating outside Turkish waters.
Strava
"Sadly, this is a contested subject within the community, and [it] falls to the teams to police their own. It's a team-driven topic. Some very big names in the [Army Special Forces] Regiment are very public with their digital presence," a former Green Beret told Insider.
"I won't name any names, but a certain controversial individual is known to post pictures of him and of PF [partner force] members on social media. I don't know why he's doing that, but my best guess would be for clout. That's disgusting in a community that takes great pride in its 'Quiet Professionals' nature," the former Green Beret said.
Such behavior is rare, but it happens and has to be approved by higher commanders, which may mean it's part of a recruiting effort, the Green Beret added.
"It's one thing pushing YouTube videos with guys jumping out of planes, shooting machine guns, or doing dives and another having a well-known individual - a celebrity - posting actual pics from downrange," the former Green Beret said. "Although I don't agree, I can definitely see the allure behind such a recruitment tactic."
Although operational security (OPSEC) is a frequent victim of sloppy digital and electronic discipline, it's not the only thing at stake.
The danger at home

US Air Force/Staff Sgt. Whitney Amstutz
As lone-wolf terrorist attacks become one of the few effective ways to strike Western societies, an association with the military can be dangerous not only to a special-operator but to their family as well.
Social media and professional networking sites, such as LinkedIn, make it fairly easy to spot and target conventional troops and commandos.
From 2015 onward, ISIS, which was fairly competent in cyberwarfare, posted names, photos, and residential addresses of thousands of US troops and called on its supporters in the US to attack them. In total, ISIS published the information of close to 20,000 US service members.
Even with the danger of a domestic terrorist attack, which remains relatively low in most Western countries, personal security (PERSEC) isn't a major consideration for most service members, including troops in several special-operations units.
But now that the main threat doesn't come from small terrorist groups but rather from near-peer competitors, such China, Russia, or even Iran, personal security and signature management becomes a real consideration for thus far unaffected military demographics.

US Army/Sgt. 1st Class Christopher Klutts
"It's very easy to map out the network of an individual just by using Facebook. Instagram is harder because of the private account option," a former Delta Force operator told Insider. "Sometimes you can find more about him and his activities not from his account but from those of his family members and friends."
"Generally, guys know to be careful, but it's hard to police others who aren't familiar or accustomed with personal or operational security. Some of the worst offenders are tagged pictures, family photos, and check-ins," the former operator added.
Digital security is more important at higher tiers in the special-operations community. The "best bet" for members of some units would be just to avoid social media and other technology that can reveal their whereabouts, the former Delta operator told Insider.
"Although these are the guys who know what not to do, it occasionally happens, as it happened with those Brits in Syria," the former operator said.
Users may skimp on digital security because they believe they have nothing to hide or that they can remain nameless in a very big pool of data. These special operators' cases show that a knowledgeable person could use that data to pinpoint not only you, but your friends and family too.
